Announcing Oak 1.0
Today the Gaiwan team is proud to announce the 1.0 release of Oak, a independent, open source, self-hosted Identity Provider. Oak supports OAuth 2.0 and OpenID Connect, making it ideal for providing access to multiple self-hosted or SaaS services with a single identity, a single login. Oak supports 2FA through standard Authenticator app codes.
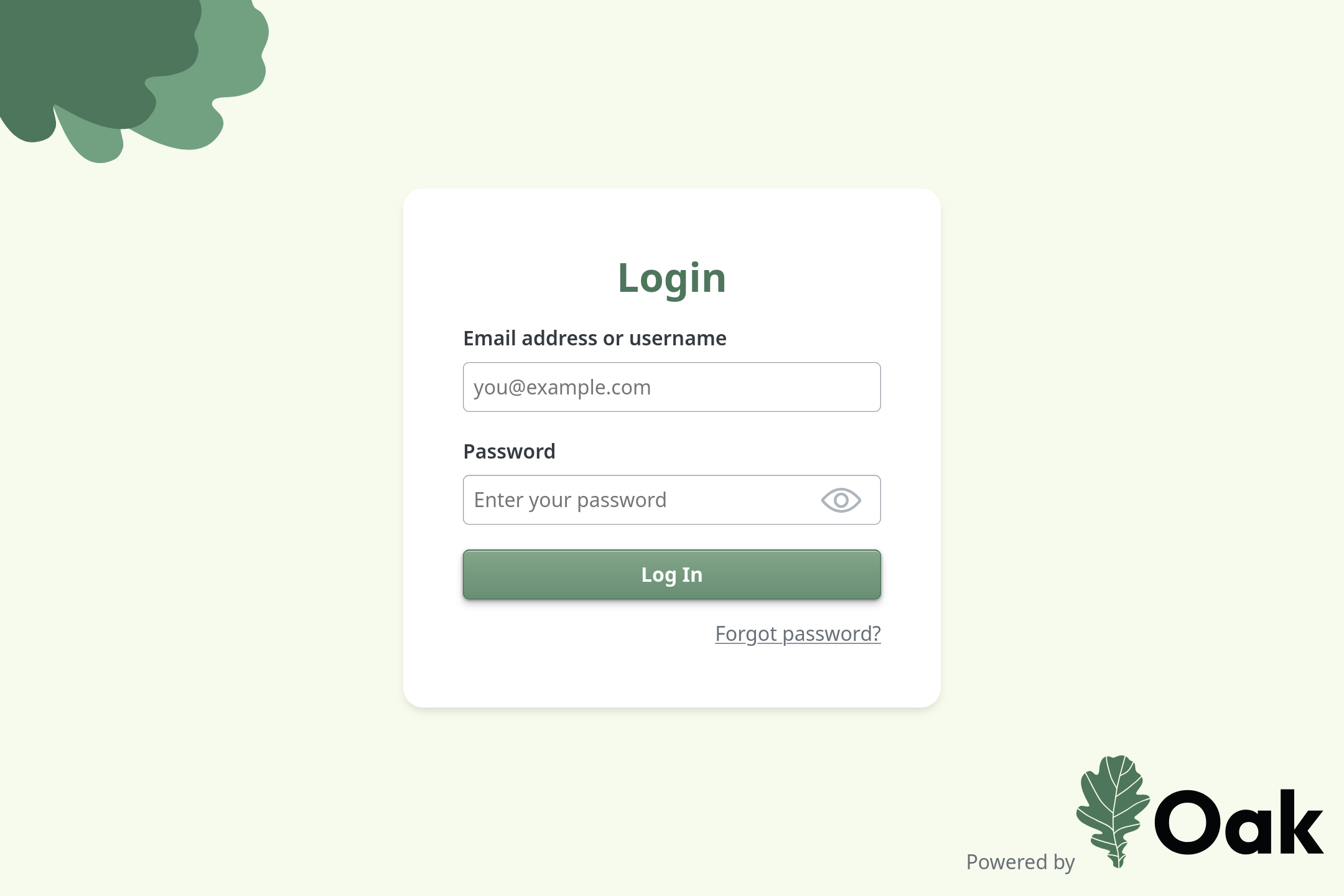
Oak is "headless" in the sense that it doesn't have a Management UI. Setting up user accounts or creating OAuth Applications is instead done through the command line. This makes Oak emminently scriptable.
Work on Oak started in August 2025, so it's still a fairly young project. Nevertheless, to keep ourselves accountable we set a deadline to have a first public release before Christmas. The past few days were spent on documentation and an installer script, as the final capstone. We really want to make it as easy as possible to get started with Oak. We'd love to hear from you if we succeeded!
Why create a new IAM/IdP product when there are already a number of excellent Open Source options available? We have a few reasons. After working on IAM and OAuth related solutions for a number of different clients, we felt we had built up the necessary expertise, we wanted to channel that into something we could present to the world. It was also a challenge to ourselves to really put out a Product that was ours. We invest a lot of time, effort, and love into other people's products. We wanted something that was really ours that we could point at and be proud of.
At this point we mainly hope to differentiate ourselves through ease and simplicity. If you are self-hosting services which support single sign-on through OpenID Connect, then Oak should be the easiest way to provide a single login to your users. We'd love to hear from people if we managed to clear that bar!
We also believe there's room for an independent, relatively low-tech IAM/IdP, that's not controlled by a major enterprise, with European roots, based on high-fidelity implementations of published standards. We are already using Oak ourselves to provide a "Gaiwan identity" that the team uses to log into our Forgejo instance, and plan to use it for many other self-hosted services going forward.
Oak is built in Clojure and runs on the JVM. For most people this doesn't matter, it's just another containerized application like any other, but Clojure teams might want to pay attention. In addition to publishing an OCI-compatible container (for use with Podman or Docker), we publish Oak as a library to Clojars, meaning you can embed it into your application, so you get login pages, password reset emails, 2FA, and more. This use case isn't documented or well developed yet, but it's an interesting secondary purpose for Oak that we're excited about.
In parallel with Oak we're also developing an OAuth testbed, which can validate the spec compliance of any OAuth 2.0/OIDC server, including Oak itself.
We have a lot of ideas for the future of Oak, but much will depend on the feedback and interest we get from this first release, so do reach out and tell us what you think.
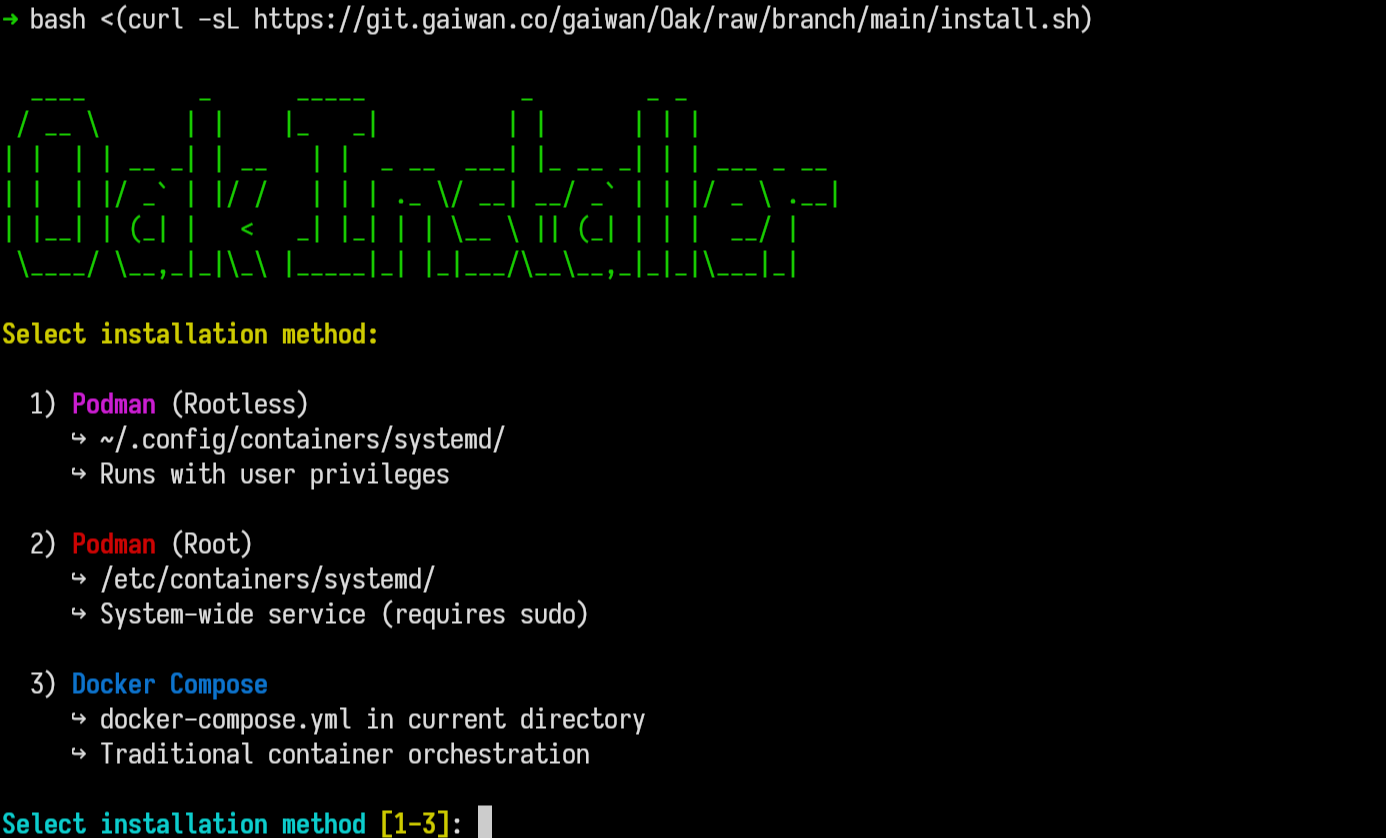
You can find Oak on the Gaiwan Forgejo instance. Follow the documentation links from there to learn how to set it up and configure it. Or if you're feeling adventurous, simply run the installer scripts, and follow the prompts.
bash <(curl -sL https://git.gaiwan.co/gaiwan/Oak/raw/branch/main/install.sh)
You can get in touch on the Fediverse or via email. You can also comment on this post on the r/selfhosted subreddit.

Comments ()